
Technical Consulting
In our digitized world, how an organization protects its data is as essential as the data itself. No one knows when the next cyber attack will hit. A planned defensive approach and constant vigilance are critical to successful navigation through known risks and unpredictable threats. At Rialya Tech, we plot a customized course towards tightened security, while considering your business objectives, budget, and culture. Our team of security experts will implement systems and protocols to fortify your defenses and help combat threats that continue to increase in both frequency and severity.
For more information, please click on any of the options below.
Vulnerability Assessments
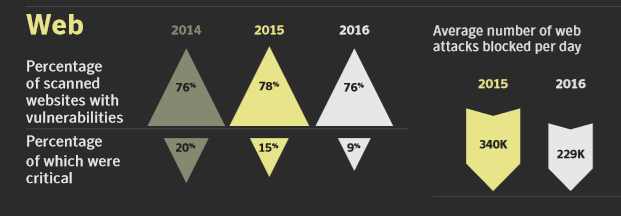 As time passes, the number of vulnerabilities remains fairly constant. As humans update applications, unintentional human error occurs, and those errors create opportunities for a hacker to exploit. The management of vulnerabilities is an ongoing process.
As time passes, the number of vulnerabilities remains fairly constant. As humans update applications, unintentional human error occurs, and those errors create opportunities for a hacker to exploit. The management of vulnerabilities is an ongoing process.
What is a vulnerability assessment?
1. A scan of your network using software that will identify ways an an attacker could access or damage your systems.
2. This service is required to pass compliance audits and can give your business essential insight into your IT processes and procedures.
Rialya Tech will run the scan on your environment, provide a report of the prioritized results, and walk you through the issues and suggested remediations. If you’d like Rialya Tech’s help with completing the remediation, we’re happy to assist.
Penetration Testing

Fundamentally, any sort of security work for a company tries to answer one simple question: “How can a hacker break into my network?” A penetration test (or “pentest”) answers that question by actually doing so.
In a formal pentest, Rialya Tech will sit down with you and define the scope of a pentest – what systems you want tested, who should know of the test, success conditions, reporting standards and details, and any other pertinent information. Our team will then put on their “hacker hats” and try to hack into your system. We’ll utilize state-of-the-art tools to gain access to as many parts of your network as we can, with the goal of compromising machines or finding sensitive data. Afterwards, we’ll write up a report detailing our findings and what can be done to remediate them. Our pentest process allows for you to remediate any issues we find. We’ll then test again to verify your efforts.
We’re more than happy to sit down with you and discuss how a pentest can help you secure your network and maintain compliance with federal standards.
Managed Firewalls
 Rialya Tech is proud to partner with Fortinet to provide firewall sales, configuration, and management. If you need a new firewall solution, we can introduce you to the best fit for your needs. If you’re looking to upgrade or switch manufacturers, we can provide guidance there as well. If you already have the equipment you want, but need assistance in installation, configuration, or monitoring, we’re happy to help.
Rialya Tech is proud to partner with Fortinet to provide firewall sales, configuration, and management. If you need a new firewall solution, we can introduce you to the best fit for your needs. If you’re looking to upgrade or switch manufacturers, we can provide guidance there as well. If you already have the equipment you want, but need assistance in installation, configuration, or monitoring, we’re happy to help.
For our monitoring services, our team reviews all logs and security events, evaluates any issues you have, and either will fix them directly or provide your team with the exact steps needed to handle them. We understand there’s a lot to cover when it comes to firewalls. Gigabytes of logs, myriad alerts and alarms, hundreds or thousands of issues to prioritize. It’s easy to get overwhelmed, so let’s partner up. We’ll handle it all so your team doesn’t have to.
If you don’t use or don’t want to use Fortinet, Rialya Tech will still happily assist. We have years of experience with Cisco, Juniper, and other firewall vendors, and can easily handle the maintenance or monitoring of any firewall you have.
IoT, Wireless, and Mobile Device Security
 We at Rialya Tech pride ourselves on staying up-to-date on the latest technology trends. The increase in mobile phone usage (to the point of replacing desktop computers), the rise of cloud computing and the Internet of Things, we’ve been watching them – and more – since the beginning. We’re happy to share our years of experience in these emerging trends with any client who would like our help.
We at Rialya Tech pride ourselves on staying up-to-date on the latest technology trends. The increase in mobile phone usage (to the point of replacing desktop computers), the rise of cloud computing and the Internet of Things, we’ve been watching them – and more – since the beginning. We’re happy to share our years of experience in these emerging trends with any client who would like our help.
The Internet of Things
Generally speaking, we can define the “Internet of Things” (IoT) as “a system of interconnected devices, connected to a wider network (such as the Internet), that can exchange data without human interaction.” Devices considered part of the IoT include security cameras, “smart home” devices like programmable thermostats, SCADA control devices, cars with on-board software, and wireless-enabled medical devices. We at Rialya Tech can help with:
- Secure design of networks with IoT components
- Proper end-user security awareness training regarding the IoT
- Security analysis, monitoring, and assessment of IoT devies
Wireless Device Security
Think your wireless network is ready for production deployment? Think again. At Rialya Tech, we’re experts in wireless network design, use, security. We can offer:
- Secure wireless network design
- Review of existing wireless network configurations, with advice on how to better configure and secure your devices
- Penetration testing and information discovery, ensuring that attackers can’t use your wireless networks against you
- Resiliency and redundancy analysis, especially under hostile conditions
Mobile Device Security
Nowadays, it’s incredibly uncommon for your employees to not have their own smartphone. Due to this “always on” nature of our daily lives, it makes sense for savvy IT executives to integrate use of personal devices into security policy. These “bring your own device” policies can improve employee satisfaction and reduce costs, but at the potential costs of introducing security weaknesses into your environment. But don’t let that stop you – embrace security from the beginning and reap the benefits. Rialya Tech can help with:
- Bring-your-own-device and Acceptable Use policies and documentation
- Choosing a security solution for remote connections or access to necessary resources
- Network segmentation and secure design principles, ensuring that a compromised device will not harm the rest of your network
No matter the type of solutions you need or currently use, Rialya Tech can help. We’re experts at adding value at any point in your IT process. Contact us today to learn about the custom-tailored solutions we offer.
Privacy By Design
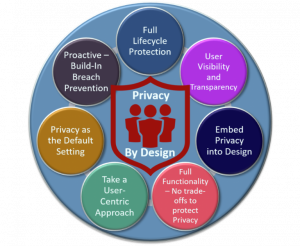
Privacy-By-Design (or Privacy-Enhanced System Design and Development) is an approach to developing systems and services with security and privacy in mind from the initiation stage of the project. By taking such an approach, organizations minimize privacy risks throughout the system lifecycle.
At Rialya Tech, we apply the Privacy-By-Design principle to all manners of system development. If you collect, store, process and share Personally Identifiable Information (PII), careful planning to ensure all system components equally protect that data is an essential part of building customer and partner trust and complying with data privacy regulations such as The Privacy Act of 1974 (USA), PCI DSS or the General Data Protection Regulation (European Union).

Whether you are configuring and deploying servers, designing and segmenting networks, defining Firewall policies, building or updating applications, defining access controls, or considering whether to share PII with trading partners, your first step in the planning process should be to conduct a Data Privacy Impact Assessment (DPIA). Unlike a security Risk Assessment, which analyzes organizational risk, the DPIA examines the risk to the Data Subjects when you use their personal data. Once you identify and acknowledge the potential privacy risks to your Data Subjects, you can appropriately design a systems environment that can withstand the majority of cyber threats and privacy risks.
In fact, most data privacy best practices and regulations require periodic execution of DPIAs. Throughout a system life cycle, your organization may update system functionality or the underlying technologies. You may change which users can access the system or what those users can do with the data. Each time you make a significant change, you should require a DPIA, in advance of authorizing the change(s).
If your organization processes personal information, Rialya Tech can help you revise your internal processes to leverage the Privacy-By-Design principle. We will provide you the tools and methods to conduct actionable DPIAs that will both influence your system development activities and meet the record keeping requirements of Data Privacy regulations.
Contact us today to discuss how Rialya Tech can help you transform into a privacy-aware organization.
Identity and Access Management
 Over 90% of data breaches originate from the actions of internal personnel. Whether they maliciously intend to steal information, or they unknowingly or accidentally give up credentials in a social engineering attack, your employees may be the weakest link in your cybersecurity defense. While security awareness training can make employees better defenders of your digital domain, the risk never completely goes away.
Over 90% of data breaches originate from the actions of internal personnel. Whether they maliciously intend to steal information, or they unknowingly or accidentally give up credentials in a social engineering attack, your employees may be the weakest link in your cybersecurity defense. While security awareness training can make employees better defenders of your digital domain, the risk never completely goes away.
Our Identity and Access Management solutions support the validation of authorized users that access your systems, and then control what those users can see and do on your network or in your customer applications.
We emphasize the “principle of least privilege” to limit access and prevent unnecessary exposure to your critical assets, even by your most trusted users. So, if an attacker manages to gain access to your network using an employee’s credentials, he likely won’t get very far.
Identification and Authentication
- We can help you create and implement a Trusted Identity platform to securely connect your users and customers to cloud, on-premise or mobile applications via:
- Single Sign-on,
- Public Key Infrastructure (PKI),
- Social Media login, or
- Multi-factor Authentication
- We develop IAM policies to ensure protection of customer identities to comply with privacy protection regulations like HIPAA or the new European Union General Data Protection Regulation (GDPR).
- Whether you are looking to devise a new IAM solution on a budget, or you have to install a prescribed IAM standard to fulfill a contractual or regulatory obligation, Rialya Tech can manage your implementation and train your system administrators and users to ease the transition to the new login method.
- We can design innovative solutions to help you deliver customized and secure user experiences.
Access Controls

- Properly implemented Access Controls restrict personnel access to only those data they need to fulfill their responsibilities. For example: Only accountants should be able to access accounting systems.By limiting what data your users can access, you mitigate your overall data loss risks.
- If the user is a victim of social attack, the attacker can only get to what the compromised user can access.
- Strong access controls prevent the nefarious user from absconding with your sensitive data.
Rialya Tech can help you implement an access control methodology that meets business objectives for security, access and transparency, while also controlling the potential impact of data breach.
- We’ll develop Access Control Policies that work in a dynamic network environment, accessed by a variety of devices, which may directly or remotely access the network.
- We will help establish formal procedures to request, authorize and provision system access, in accordance with a segregation of responsibilities principle.
- We will provide guidance to develop protocols to protect information if a system user walks away from his computer.
- We will implement physical security controls to restrict facility access to only authorized personnel.
- We will develop monitoring and record keeping procedures to ensure you can demonstrate your capabilities and you are prepared for audit.
- We’ll help identify and classify data, identify insider risks, and mitigate those risks through implementation of risk-aware access controls, governed by business owners.
- We’ll help you define the business value of various data in your control.
- We will assess the risk associated with each role in your organization.
- Then we will work with business owners to assess current access controls for relevance and necessity; making additional access and revocation recommendations along the way.
- Finally, we will design your access controls to be flexible to system or service changes, acknowledge the increasing migration to cloud environments and comply with increasingly stringent security and privacy regulations.
Contact us today to discuss how Rialya Tech can help you build a secure network environment.
Contact Us
Don't Hesitate to Contact us for any information
Call us for immidiate support to this number
+1.773.750.0685 ORAlso Send mail to this email ID
support@rialyatech.com



