
Manage Security Services
The Rialya Tech security team monitors your systems 24×7 using AlienVault technology complete with Threat Management Tools. We review and evaluate system activity in real time through reported alerts and alarms. We then apply our expert knowledge and determine activity that requires notification to your IT team to minimize and mitigate risk of system intrusion. Further we assist management in best practice response to these potential threats working as a member of your IT team.
Rialya Tech Security Engineers and Technicians are dedicated to the identification and analysis of cybersecurity incidents and events within our clients’ information systems. Rialya Tech correlates the anomalies and incident findings of its clients to provide advisories of known threats to all clients creating a wider knowledge set than possible working in just one instance.
Rialya Tech will never remove confidential data from client environments. Rialya Tech and AlienVault systems rely only on security related log data and configured alerts to monitor the security health or exceptions to “normal” security state of client information systems.
The Rialya Tech team are experts on the various tools AlienVault offers and leverages that knowledge to support your organization. The toolbox we optimize for your organization includes:
- Security Incident and Event Monitoring (SIEM) – The USM captures, parses, and correlates log data from security and networking devices to increase network visibility into anomalies that may be indicators of compromise.
- Behavioral Monitoring – Includes NetFlow monitoring, packet capture, service availability, and infrastructure monitoring to detect suspicious behavior that can provide early warning of malicious activity.
- Intrusion Detection – AlienVault regularly updates Network Intrusion Detection (NIDS) signatures to detect the latest threats that may affect your environment. SCS will implement Host-Based Intrusion Detection (HIDS) agents on your most critical assets.
- Asset Discovery – Uses both active and passive discovery methods. Active discovery loads network configuration to USM. Passive discovery watches network traffic and logs data in support of SIEM and Behavioral Monitoring.
- Vulnerability Detection – USM continuously monitors network traffic comparing it to known vulnerabilities for immediate threat discovery. Active detection scans individual systems and subnets. We will run vulnerability scans on a mutually-defined, risk-informed frequency.
- Based on quantity of data running through each device; the criticality of the device; the known vulnerabilities associated with the device; and the schedule of automation jobs on, and usage of, each device.
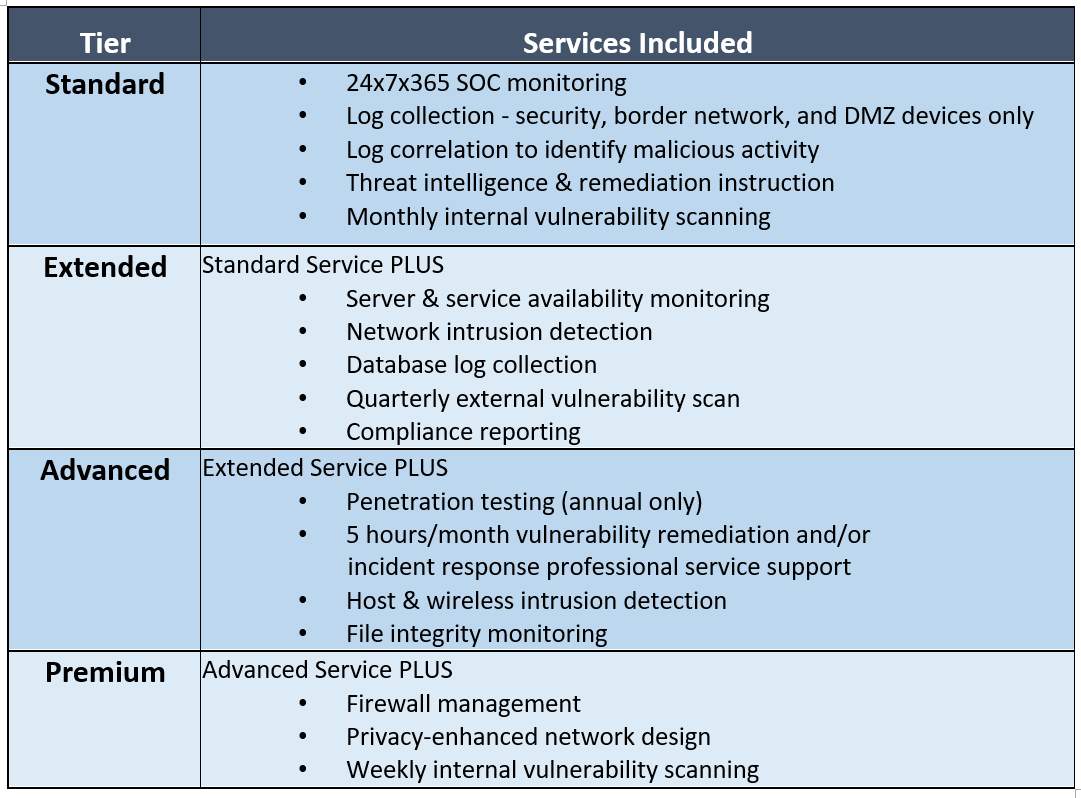
Our Service Tiers
Rialya Tech offers a tiered service offering to provide options that balance functional needs and cost.
- Our flexible approach facilitates immediate, cost-effective cyber protection benefits, and allows the client to evolve into a more mature and robust cyber security posture, in line with budgetary planning cycles.
- Each tier provides a greater level of protection, while shifting security responsibility to our trained professionals dedicated to the defense of our customers.
Contact Us
Don't Hesitate to Contact us for any information
Call us for immidiate support to this number
+1.773.750.0685 ORAlso Send mail to this email ID
support@rialyatech.com



